Strange 7078 Error
The 7078 Error "The Advantage Database Server cannot authenticate the user" is a very straight forward error message. Essentially the username and password supplied for the Advantage Data Dictionary (database) were incorrect. This error is easily corrected by supplying the proper username/password combination.
However, what if you get this error when you supplied the correct username and password or stranger still when you are connecting to a directory of free tables. The answer lies in the Advantage error log (ads_err.adt) where you need to look for other error codes that occurred at approximately the same time as the 7078 error. See the example below:
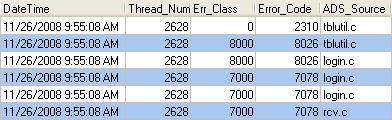
In this case the important error is the 8026 "Error obtaining server drive information from server and share names". To fix this error verify that the path is correct, the path can be located in the FileName column of the error log, and that the share exists.
File Errors with Version 9.1
In version 9.1 of Advantage we changed the way that files are opened when in proprietary locking mode. In the past these tables were opened in a "deny write" mode which allowed other programs to access them in read-only mode. This could lead to index corruption since other programs could lock bytes in the file causing Advantage reads and writes to fail.
With version 9.1 tables are now opened so only the server can access them. If you still need to access the files as read-only you can set proprietary locking to be non-exclusive. This is done by setting the NONEXCLUSIVE_PROPRIIETARY_LOCKING flag in the registry (Windows) or in the Advantage configuration file (Linux and NetWare).
You can access data concurrently with Advantage and a non-Advantage application using compatibility locking when using DBF files. Advantage proprietary files (ADT) are always opened using proprietary locking.
6097 Errors
The 6097 "Bad IP address and/or bad port specified in connection path or in ADS.INI file" seems like a very strait forward error. It can usually be resolved by verifying that the correct IP address and port number have been specified. You may also need to ensure that any firewalls allow UDP traffic for the specified port. With version 8.1 or newer you can specify TCP (see this post for details) on the clients instead of UDP.
There is one other situation where you may be receiving 6097 errors. This error can be reported when you are evaluating Advantage. If the evaluation code has expired the server will not respond to any client requests and the client will report a 6097 error as described in this KB Item. This behavior has changed in version 9.1 which will now report a new error code 7046 "Evaluation Period Expired"
Windows /3GB Switch
A 32-bit operating system allocates 4GB of virtual memory address space. This is split in half with 2GB allocated to the operating system (kernel) and the other 2GB reserved for applications. This default setting can be overridden by using the /3GB switch in the Boot.ini file. This changes the virtual memory allocation allowing for 3GB of virtual memory address space for applications and the other 1GB for the operating system.
This can cause some unexpected consequences and may not improve performance. We do not recommend using this switch when running Advantage on a 32-bit Windows machine. In order to address more memory with Advantage use a 64-bit operating system and the 64-bit version of Advantage.
For more information about the /3GB switch I recommend this series of articles by Raymond Chen from the Windows team.





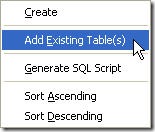 The best part of data dictionaries is how little effort is required to get started using them. It is extremely easy to add existing tables to a data dictionary using ARC. You simply right-click on the tables icon in the tree view and choose "Add Existing Table(s)". A file open dialog will be displayed allowing you to select all of the tables you wish to add to your data dictionary. This will also include any structural index files associated with the table.
The best part of data dictionaries is how little effort is required to get started using them. It is extremely easy to add existing tables to a data dictionary using ARC. You simply right-click on the tables icon in the tree view and choose "Add Existing Table(s)". A file open dialog will be displayed allowing you to select all of the tables you wish to add to your data dictionary. This will also include any structural index files associated with the table.