I have been using Virtual Server R2 for almost two years now and it has proved quite useful as a testing environment. I was able to use my it to create both a Windows 2003 and Windows 2008 cluster. I have used these clusters for testing and documentation purposes. There is an excellent tutorial from Microsoft on creating a Two-Node cluster using VirtualServer which describes creating a Windows 2003 cluster in great detail. I used this to create my first test cluster and as a starting point for creating a Windows 2008 cluster.
Since you will be creating several VMs for your virtual cluster environment I recommend creating a Parent Virtual Machine, as described in the Micriosoft tutorial. Make sure you apply all the updates, security patches and the virtual machine additions. You will need to update Virtual Server to get the latest additions which support Windows Server 2008. You should then run sysprep on the image to ensure that any VMs created from this base image will contain unique security information.
You can create an answer file before performing the sysprep which will greatly simplify the install process. By running sysprep with an answer file you can completely automate the final steps of the install process. Therefore when you create new VMs based on the parent disk it will be like starting up a brand new machine from right out of the box. I chose to set my license key, timezone, screen resolution and networking setup. So when I create new VMs everything is automatically set to my base settings.
Microsoft supplies a graphical tool which helps create an answer file. For Windows 2003 you can use SetupMgr.exe which will walk you through generating an answer file. You can get the latest sysprep update for Windows 2003 server here. For Windows 2008 I recommend getting the Windows Automated Installation Kit (AIK) which you can get here. It is a bit more difficult to use than setup manager but it is worth the trouble.
Once you have run sysprep on the parent disk go to the vhd file and mark it read-only. You can now use this disk as a parent disk for new virtual machines. This is done by using a Differencing Disk which creates a unique disk based on the specified parent. This saves both a lot of time and disk space.
With your parent(s) created you are ready to build your cluster environment. To create a cluster you will need the following items:
- A domain controller
- Shared storage
- Two Networks
- Two VMs for nodes
- Win 2003 Server Enterprise or Win 2008 Server Enterprise
All nodes in a Windows cluster must be members of a domain so you must have a domain controller. To keep everything in the same place I configured a VM running Windows 2003 Server as my domain controller. I use this domain controller for both a Windows 2003 and 2008 cluster. I also configured three networks; Public, Private and Storage. These networks run in Guest Only mode so they are not accessible to other machines. This isolates my test network making it easier to manage.
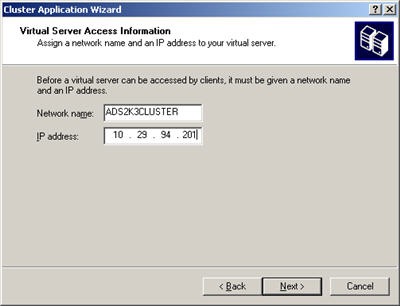
The Public network is used to communicate to the cluster and its applications. The private network is used for communication between cluster nodes, the 2003 and 2008 clusters run on separate subnets. The Storage network is used for iSCSI access from the Windows 2008 cluster.. Although this is not strictly necessary it is recommended that a dedicated network be used for the shared storage.
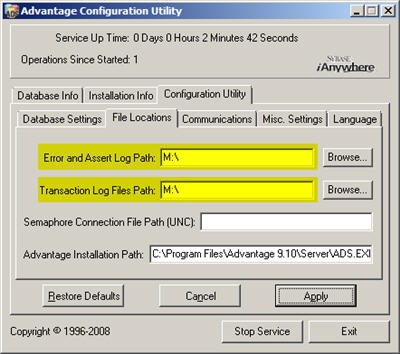
Both Windows 2003 and Windows 2008 require some type of shared storage to work correctly. Virtual Server allows up to two VMs to connect to a shared drive using a virtual SCSI controller. This provides basic functionality for a Windows 2003 Cluster but only allows for a single shared drive. Windows 2008 Clustering does not use this shared SCSI system so you must use an iSCSI solution instead. Windows 2008 includes an iSCSI initiator which allows the server to connect to shared storage over the network. However, you will need additional software to create an iSCSI target. This is included with Windows Storage Server which is an embedded solution from Microsoft and difficult to obtain. I used StarWind software to create iSCSI targets on my Domain Controller that I could use from the new cluster. It is a very lightweight download and simple to install and configure. There is a free version which limits the disk size to 2GB but is perfectly adequate for testing.
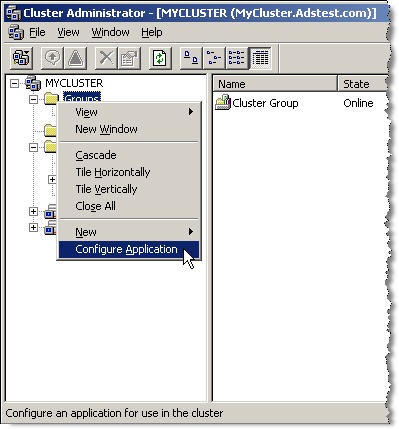
Windows 2003 Enterprise includes the Cluster Manager by default, however, you need to add the Failover Clustering feature both VMs that will serve as Windows 2008 cluster nodes. This can be done from the Initial Configuration Tasks dialog under Customize This Server. Once the Failover Clustering feature has been installed you create the cluster by going to Control Panel->Administrative Tools->Failover Cluster Manager.
Before creating a new cluster verify that the shared storage has been initialized and formatted. You will also have to configure each node to access the shared storage. Until the cluster is completely installed you will need to configure the storage with only one of the nodes running at a time.
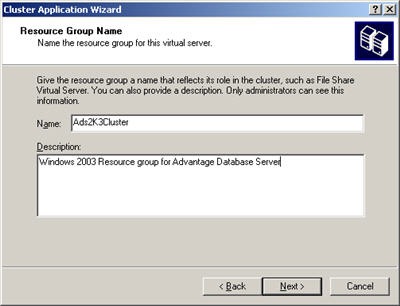
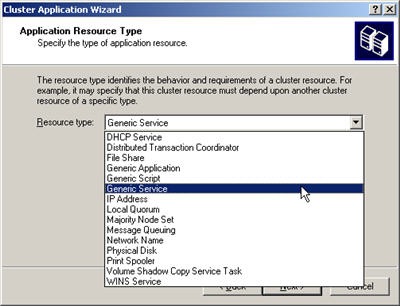
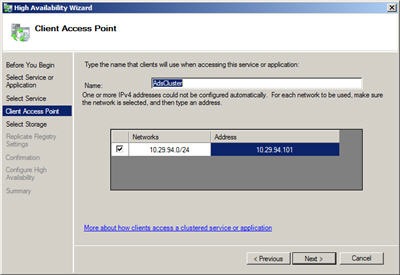
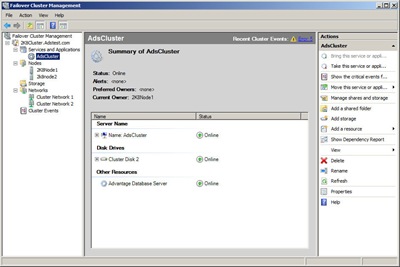
Now that all the prep work is done you are ready to install your cluster. Boot up node 1 and start either the Cluster Manager or Failover Cluster Manager. This will start the Cluster Wizard which will walk you through creation of your cluster. The Failover Cluster Wizard will give you an option to run the Validate a Configuration Wizard, I recommend doing this to verify that you have setup your VM environment correctly. After you have successfully configured the first node start your second node and add it to the cluster using the Cluster manager.
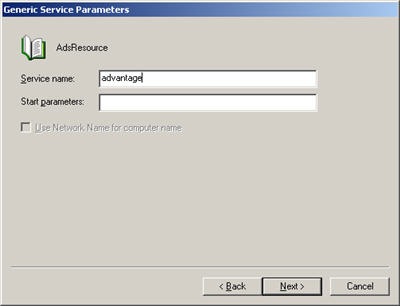
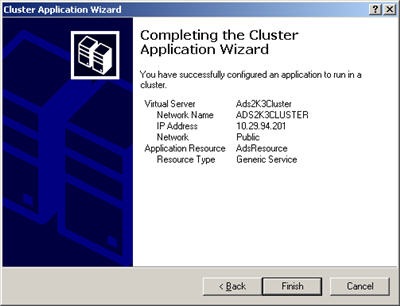
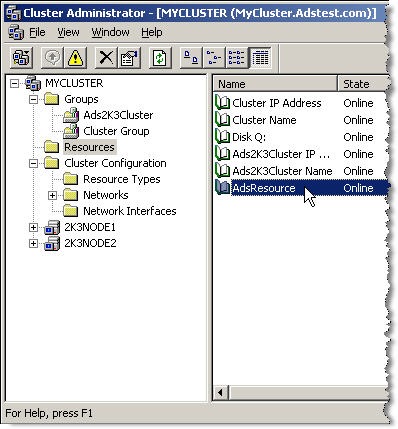
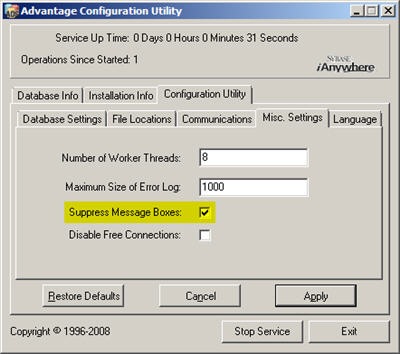
Now that you have a virtual cluster environment setup you can install Advantage.