Clipper IP Libraries
Advantage provides support for IP communication from Clipper with a helper application called ADSDOSIP. This provides a bridge between the Clipper application and Advantage so there is a performance degradation when using it. However, it can be used to extend the life of your clipper applications in a TCP/IP only environment.
ADSDOSIP and its associated libraries; axipbcom.lib, axipcomm.lib and axipxcom.lib are included in the Clipper Install. However, it is not installed by default you must choose a custom install and ensure that IP for CA-Clipper is selected.
Accessing Data on a NAS
For best performance data which is accessed through Advantage Database (REMOTE) Server should reside on the machine where the Advantage service is running. However, you can access data with the Advantage Server which resides on another server. This is done using a Server-Side Alias which were introduced in Advantage version 8.0.
If the data being accessed through Advantage Database Server is not physically located on the machine running the Advantage service you may experience some performance or corruption issues. Since the data is stored remotely the server has to transfer the data across the network in order to use it. If the connection to the remote data is lost every user connected to the server will no longer be able to access their data.
Replication with Different Server Versions
Replication was introduced in version 8 of Advantage and has been enhanced in version 9. Replication is configured in a Data Dictionary by defining a publication, the tables to be replicated, and one or more subscriptions, servers to push the changes to.
The publisher pushes the changes to the subscriber(s) by making a connection and sending the appropriate commands. Essentially the publisher is a client to the subscriber(s), therefore, it consumes a user license at the subscriber and must be the same version or older than the subscriber.
This means that an 8.x server can replicate to a newer 9.x server but a 9.x server will get an error when attempting to replicate to a 8.x server. You can get more information about replication from the Replication Overview topic in the help file.
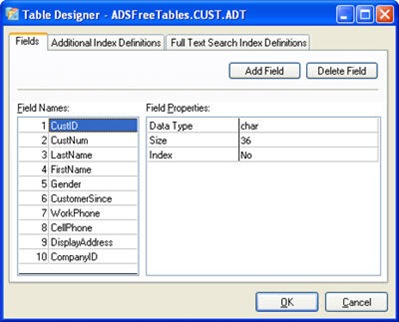
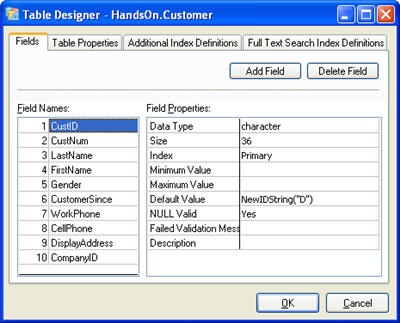
Setting Table Collation Sequence
Advantage 9 supports many new collation sequences as well as the ability to set the collation sequence per table. In prior versions the collation sequence was set on the server and was applied to all tables. If this collation sequence was changed all of the indexes would have to be rebuilt. If you attempt to open a table with an incorrect collation sequence you will receive a 5209, Collations do not match, error.
Version 9 introduced a new API call AdsOpenTable90 which includes an option for setting the collation sequence to use when opening the table. When using the TAdsTable component in Delphi the collation sequence for the table is set on the AdsCharType property.
The specified collation sequence is loaded dynamically by the server and used with the table. These collation sequences are stored in a table named adscollate which is distributed with the server. When using local server you must include this table in your application path if you need to use FoxPro collations.






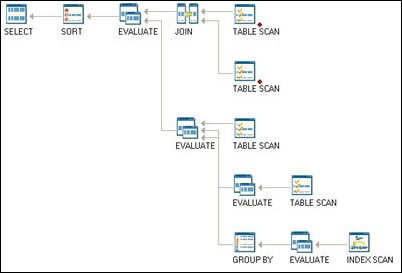
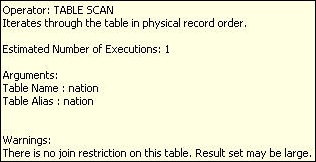 By hovering over an object (i.e. TABLE SCAN) additional information about the execution step will be displayed in a popup. The popup (example on right) displays; the operation with a description, number of executions, arguments and any warnings. In this case there is a warning on the Join condition not being optimized. The data shown in this popup is also displayed in the Data window which is normally docked at the bottom of the SQL Utility window. Detailed information about each execution step is contained in the data table.
By hovering over an object (i.e. TABLE SCAN) additional information about the execution step will be displayed in a popup. The popup (example on right) displays; the operation with a description, number of executions, arguments and any warnings. In this case there is a warning on the Join condition not being optimized. The data shown in this popup is also displayed in the Data window which is normally docked at the bottom of the SQL Utility window. Detailed information about each execution step is contained in the data table.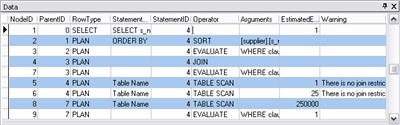
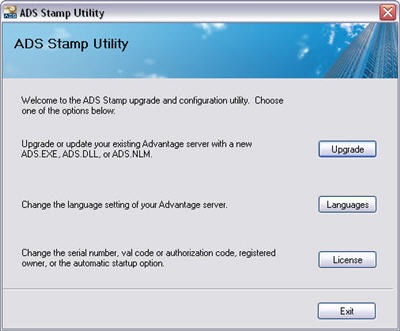
 If you are upgrading from a previous version of Advantage the 9.0 install will detect and uninstall the previous version of the server. You will be prompted to stop the service and perform the uninstall of the previous version. This functionality was added in the installer beginning with version 8.0 of Advantage.
If you are upgrading from a previous version of Advantage the 9.0 install will detect and uninstall the previous version of the server. You will be prompted to stop the service and perform the uninstall of the previous version. This functionality was added in the installer beginning with version 8.0 of Advantage. Advantage service updates are distributed as a full install which will upgrade to the latest version of the server. Therefore there is no need to install version 9.0.0.0 before installing the latest service update, currently 9.0.0.7. If Advantage is already installed the installer will detect the currently running server and read the license information. The user is prompted to use the current information eliminating the need to enter any license information during the upgrade.
Advantage service updates are distributed as a full install which will upgrade to the latest version of the server. Therefore there is no need to install version 9.0.0.0 before installing the latest service update, currently 9.0.0.7. If Advantage is already installed the installer will detect the currently running server and read the license information. The user is prompted to use the current information eliminating the need to enter any license information during the upgrade.