High availability (HA) is a topic that I encounter frequently when talking to database developers. With high quality hardware at very reasonable prices smaller companies are considering high availability. This becomes critically important for companies that provide 24X7 access to information. For these companies down time means money lost and unhappy customers.
Earlier this year I wrote a white paper about high availability and Advantage. It discusses HA in very general terms and offers information about planning an HA solution. You can read the white paper here. William Brewer wrote a very good article on Simple-Talk.com "Database High-Availability: Soup to Nuts" which is also worth a look. Finally there is a Tech-Tip which highlights the Advantage features which can be used for providing an HA solution.
Since this topic comes up quite often I thought I would revisit some of these features. In particular I will be discussing a Warm Standby solution using replication or server-side aliases.
Advantage Replication provides an excellent mechanism for providing a Warm Standby solution. By configuring the database to replicate to a standby server a current copy of the data is always available. As changes are made on the primary server these changes will be pushed to the standby server in real time. If the primary server fails users will simply need to connect to the standby server and continue working.

There are a few caveats to this solution. First users will receive an error when the primary server fails, most likely 6610 "Client timeout". You will have to have some sort of mechanism within your application to allow users to change to the standby server path. Second the data on the standby server should never be changed unless the primary server is not available. Replication is not the same as synchronization so altering the data on both the primary and standby servers at the same time may produce different data at each server. Therefore you may need to control when users can connect to the standby server which can be accomplished by disabling logins to the standby database. When the primary server fails the administrator enables logins on the standby server and tells the users to change the connection path for the application.
When the primary server has been repaired you will need to copy the data from the standby server back to the primary server. You should do this when all users are logged off the system. Copy the data from the standby server to the primary server and verify that replication is setup and enabled. Once this is finished both servers will have the same data and users can be allowed onto the primary server again.
Another way to provide warm standby is the use of Network Attached Storage (NAS) or Storage Area Network (SAN) devices. These devices are designed to be shared between multiple systems allowing two or more machines to access the same data. Advantage uses server-side aliases to connect to external devices for data access. With this solution the database remains in the same location and is simply accessed by the available server.
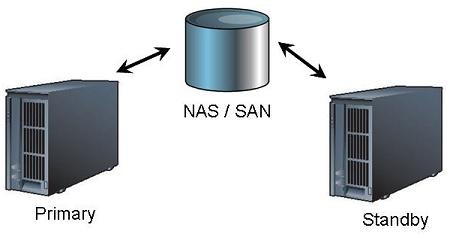
Advantage data dictionaries and tables can only be opened by one server at a time. Therefore, both servers can not have the data open simultaneously which means that whichever server opens the data first is the one that all users must connect to. Another issue with this solution is the potential for a single point of failure. If the NAS/SAN is not available then the data will not be available whereas with the replication solution the data is stored on both servers. To use this solution a fault-tolerant NAS or SAN would reduce the risk of failure but raising the expense.
Both of these solutions can greatly increase the availability of your data. Having a second Advantage server running and ready to accept requests will greatly reduce the amount of down time your users experience. You will need to educate your users on how to respond to a failure of the primary server. Your IT staff or "computer guy" will also need to respond quickly to determine why the primary server failed so it can quickly be fixed. HA solutions are resource intensive and require training and setup but for companies who need them they are invaluable.
As a final note; an HA solution is not a substitute for regular backups and a disaster recovery plan. The solutions I described above would commonly be located at the same location, therefore, you should keep an off site backup in case something happens to your office. Consider using the Advantage Online Backup features to generate backups on a scheduled basis.
 The next Advantage Technical Summit will be held in Boise, Idaho on September 10th and 11th. We have changed the breakouts to provide more flexibility in scheduling and allowing you to get to the sessions your most interested in. We will now be providing four separate sessions on SQL which will be available both days. You can register for the Technical Summit here.
The next Advantage Technical Summit will be held in Boise, Idaho on September 10th and 11th. We have changed the breakouts to provide more flexibility in scheduling and allowing you to get to the sessions your most interested in. We will now be providing four separate sessions on SQL which will be available both days. You can register for the Technical Summit here.